Workplace communication involves exchanging sensitive, often confidential employee details. This makes internal communications a perfect target for cyber attacks. Learn how to better secure your internal communications to protect your business from online threats.
Indigo, Yahoo, Adobe, Ikea, Facebook—those are just a few of the companies that recently experienced a major cyber security breach. And these are just the headline-makers; internal data breaches are becoming more common across businesses big and small.
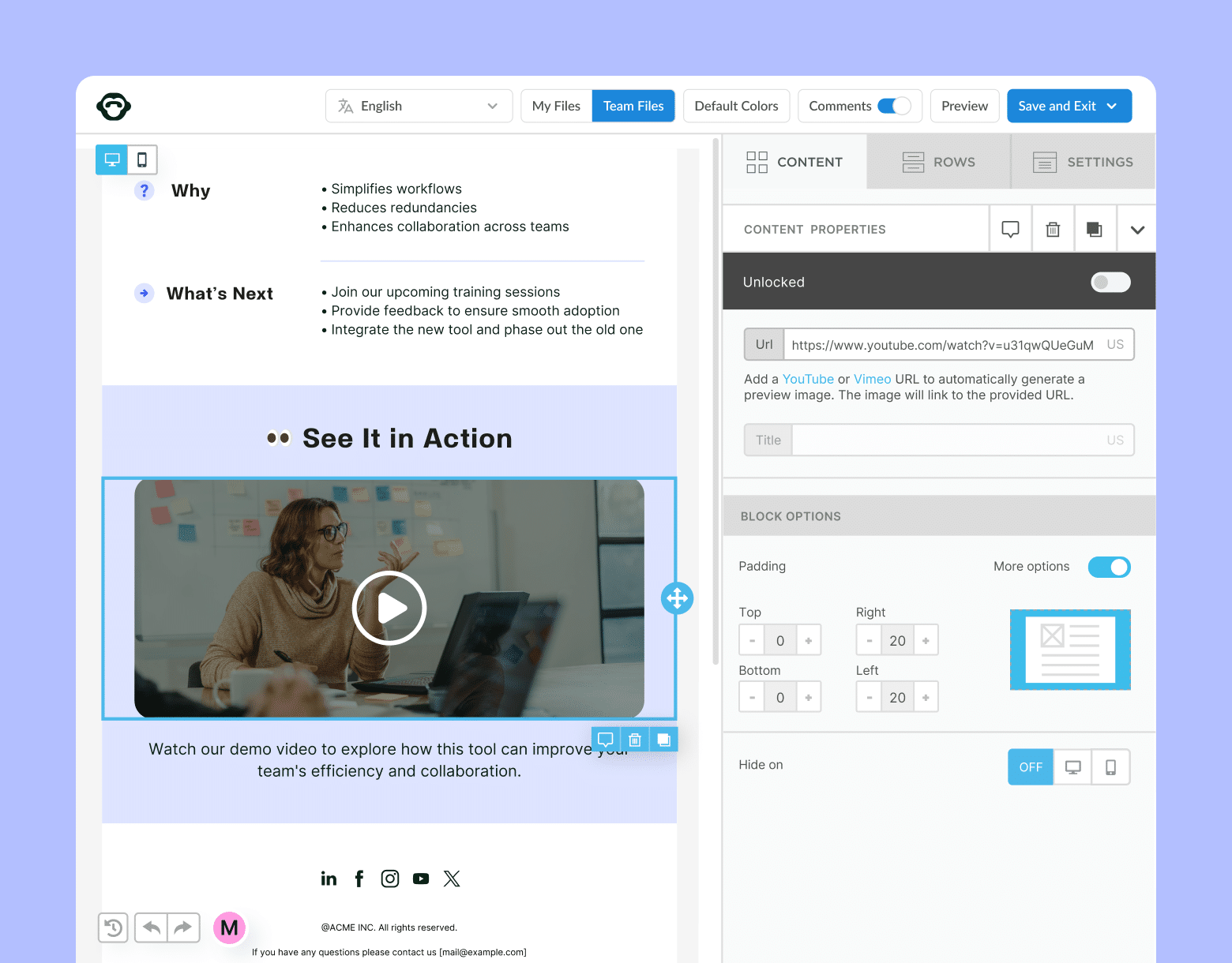
When internal email security is compromised the damage can be permanent and far-reaching. We’ll show you how to send a secure internal email in Outlook and Gmail using our internal email platform as well as how to shield all your communications against cyber threats and ensure email privacy for internal communication.
Questions we’ll answer in this blog:
- Is your internal email secure?
- How can you secure your internal email?
- How do you ensure employee email security?
- What are the best internal email security tools?
- How do you guarantee email privacy for internal communication?
Take a self-guided tour of ContactMonkey
See how our key features can streamline your internal communications.
Take product tour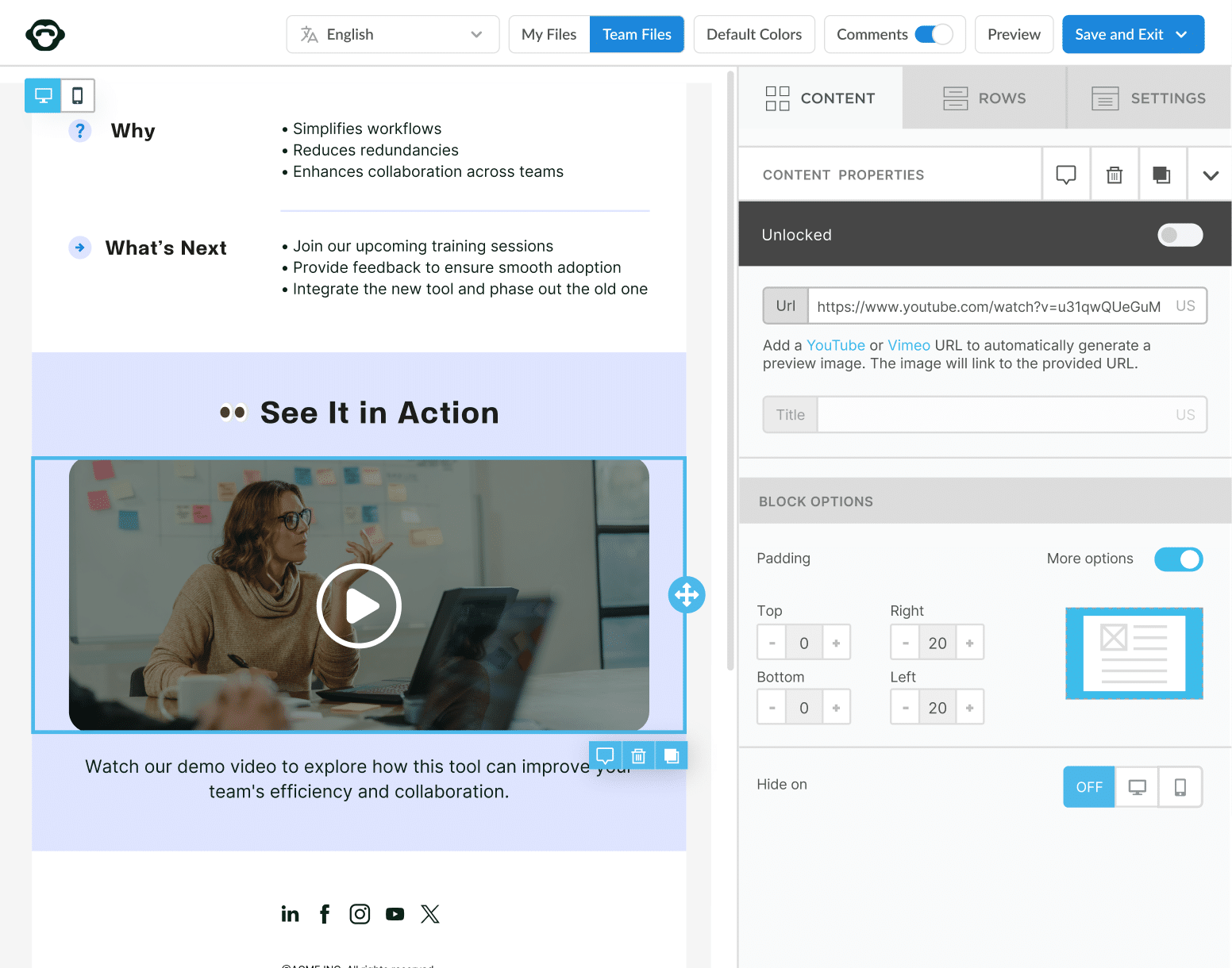
Why is Secure Internal Communication Important?
Internal communications security is essential for safeguarding sensitive employee and business information. Banking details, health insurance information, and home addresses are just some of the private data that can be exposed during an internal communications security breach.
A cyber attack on your internal communications can also create a domino effect where customer and stakeholder data becomes compromised. When that happens, it’s hard to back-pedal, repair the damage, and say ‘sorry.’
The consequences of an internal communication security breach can include:
- Unauthorized use of employee and customer data: Once exposed, this information could be exploited by malicious actors.
- Reputational damage: A security breach can severely erode trust among customers, partners, and stakeholders.
- Financial losses: Beyond the direct costs associated with remediation efforts, such as regulatory fines, organizations may also face indirect costs such as loss of employees, customers, and revenue.
- Regulatory non-compliance: Many industries have to follow regulations around data protection and privacy, such as GDPR, HIPAA, or PCI DSS. A security breach that results in the unauthorized exposure of sensitive data can lead to significant legal penalties.
- Disruption to the business: Overall, a security breach is sure to disrupt normal business operations, leading to downtime and decreased employee productivity, as well as poor employee morale and employee disengagement.
- Loss of trust: Probably the biggest long-term risk of an internal communications security breach is diminished trust on the part of staff and customers who expect organizations to protect their personal data.
Get powerful send features with ContactMonkey
Create custom audiences, increase content relevancy, and improve employee email engagement.
Learn more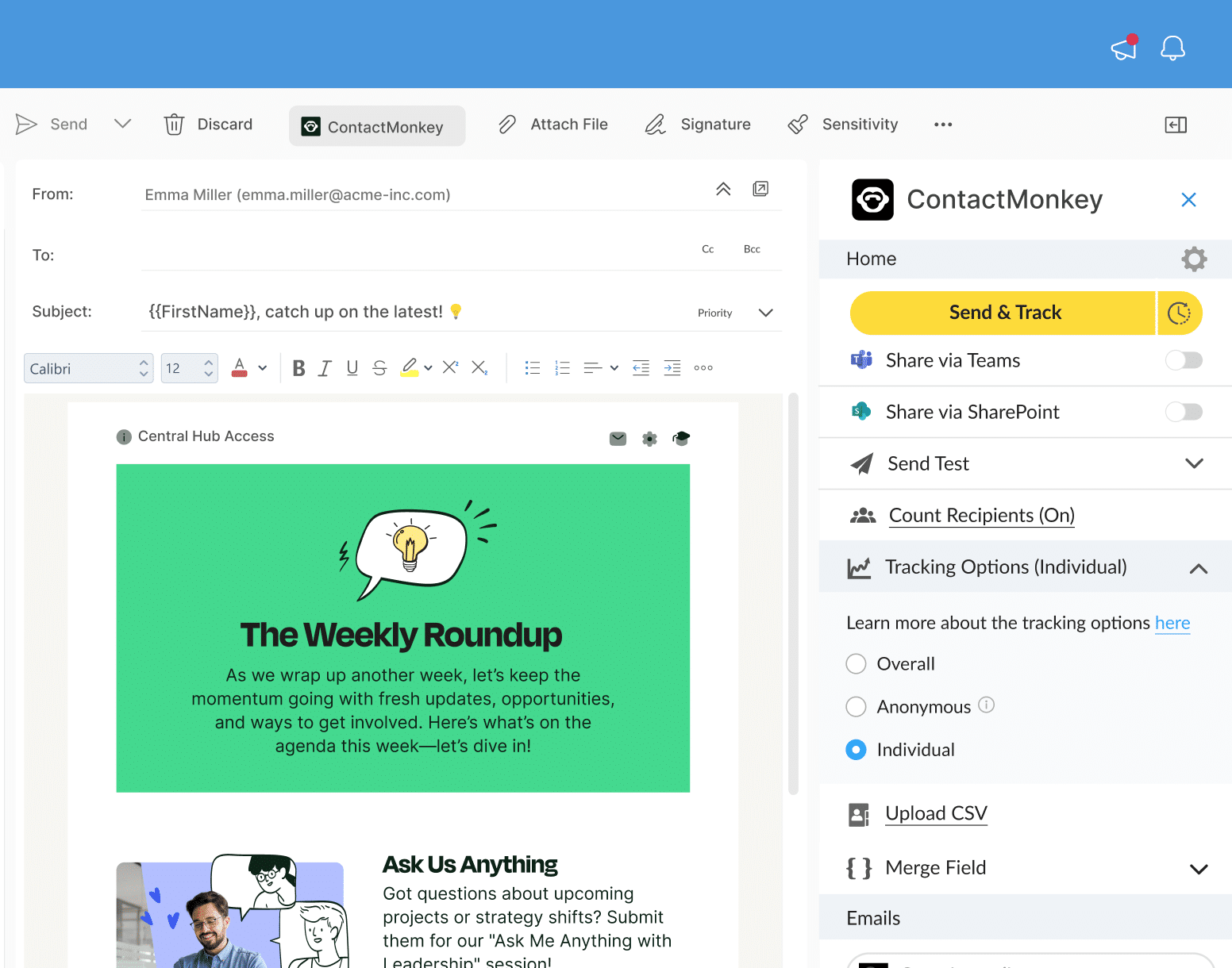
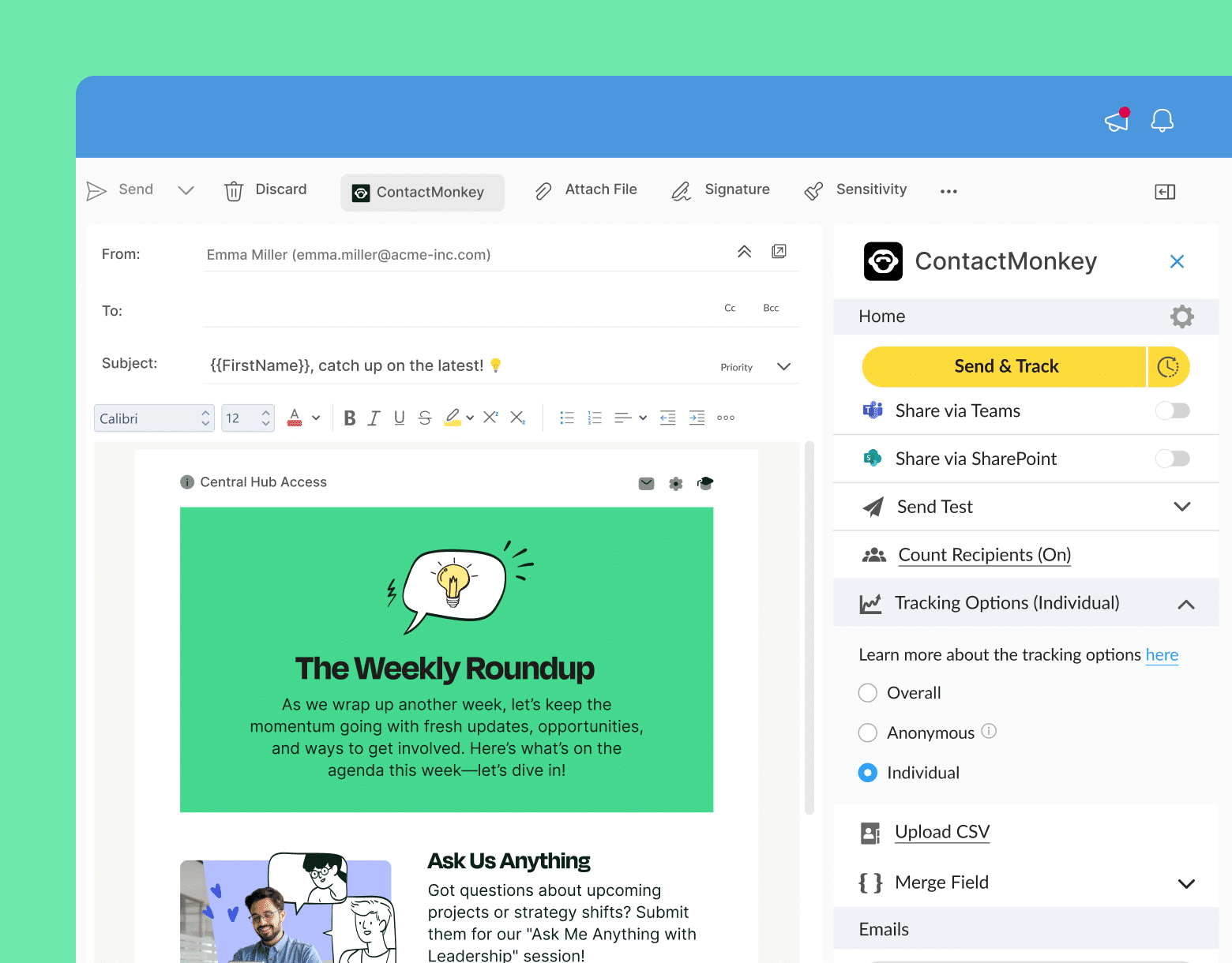
Common Methods to Secure Internal Communication
There are several ways to ensure that your internal communications aren’t vulnerable to hackers and other security threats. Here are the secure internal communication basics that you need to know today in order to protect tomorrow:
- Implement data encryption: Encrypting internal communications ensures that even if intercepted, the data compromised is unreadable to unauthorized parties.
- Ensure cloud security: If internal communications pass through a cloud service, it’s crucial to ensure the security of the cloud environment. This includes creating access controls, encryption, and conducting regular internal communications audits.
- Use secure messaging: secure internal communications platforms offer end-to-end encryption, which means only the sender and intended recipient can read the messages. Employee SMS, internal email newsletters, and intranet communications can all be secure messaging platforms with the right internal communications solution.
- Install user permissions: limiting access to sensitive internal communication channels based on user roles and permissions helps prevent unauthorized access.
10 Best Practices for Secure Internal Communication
Here are 10 best practices to ensure internal email communications security across your business:
1. Fortify your emails with secure internal communication software
The first step to ensuring internal communication security is using a secure internal communication app. The best employee email security tools include encryption, multi-factor authentication, and security certifications like SOC 2 Type 2 compliance.
2. Protect sensitive information with internal email encryption
Robust internal email encryption protocols will protect employee data and other sensitive company information, ensuring the information remains secure even if intercepted. Both Outlook and Gmail offer encrypted email solutions.
3. Keep out intruders with multi-factor authentication (MFA)
Require users to authenticate their identity using multiple factors such as passwords, an authenticator key, face recognition, or tokens to add an extra layer of security.
4. Control access to sensitive information
Enforce strict access controls based on the principle of least privilege (a fancy computer science term that means only people who need access to certain information for their role can access it). This ensures internal communication security by only allowing authorized individuals to access sensitive communication channels or information.
5. Strengthen privacy with secure channels
If you want an extra layer of internal communication security, we recommend making use of secure communication channels such as Virtual Private Networks (VPNs) or Secure Sockets Layer (SSL)/Transport Layer Security (TLS) protocols to transmit data securely over networks.
6. Stay one step ahead of data thieves
Keep communication software and systems updated with the latest security patches and updates to mitigate vulnerabilities and protect against emerging threats.
7. Keep employees vigilant with security training
Provide comprehensive employee training on secure internal communication practices, including recognizing phishing emails, using strong passwords, and understanding the importance of data protection.
8. Detect security risks with email tracking
Implement monitoring tools and email tracking software to detect unusual email user behaviors and respond to suspicious activities. When you notice unauthorized access to internal communication channels, respond promptly.
9. Protect your data with data loss prevention (DLP)
Data loss prevention (DLP) is a combination of strategies designed to secure and monitor internal business data. Implement DLP policies to prevent unauthorized sharing or leakage of sensitive information through internal communication channels.
10. Shield SMS messages with secure mobile devices
Implement security measures such as device encryption, remote wipe capabilities, and mobile device management (MDM) solutions to secure communication on employee text messaging tools used for work purposes.
Unlock Internal Comms Superpowers
Discover why 10,000+ rely on us. See the internal email and employee newsletter platform in action.
Book demo

How ContactMonkey Helps Your Company Achieve Secure Internal Communication
Internal communication tools and security have a close relationship—without secure software, you can’t have a secure flow of information across your business.
ContactMonkey helps your business achieve the highest level of internal communication security by providing encryption, centralized management, integration with corporate email systems, and the highest grade of compliance features for private internal emails and SMS.
Here’s a closer look at why ContactMonkey is the number one IT-trusted internal communications system:
Email tracking and analytics
With comprehensive email tracking and analytics features, ContactMonkey allows businesses to track the delivery, open rates, and engagement of internal emails. This helps organizations ensure that their internal communications are always reaching the intended recipients securely.
SOC 2 approval
If you’re wondering, is internal email secure? The answer is yes—when you use secure and private internal email software. ContactMonkey holds SOC 2 type II compliance, validating enterprise-level security for customer data according to the standards of the American Institute of Certified Public Accountants (AICPA), ensuring the highest security and compliance standards.
Single sign-on (SSO) authorization
Single sign-on (SSO) offers added security, allowing users to log in securely with existing company credentials.
Data encryption and storage on AWS
Leveraging Amazon Web Services (AWS), ContactMonkey ensures top-tier security with AES-256 encryption for data at rest and TLS v1.2 for data in transit, meeting SOC and ISO regulations.
Outlook add-in vs. external Tools
As an add-in atop Outlook, ContactMonkey enhances security by avoiding third-party server hosting, ensuring data security and email consistency. You’ll know how to send a secure internal email in outlook every time because you’re already using a secure platform.
GDPR compliance
ContactMonkey complies with GDPR, providing policies for data erasure and offering anonymous email tracking to maintain employee privacy.
Secure development
ContactMonkey follows secure development lifecycle principles and adheres to OWASP Top 10 recommendations, ensuring robust security in all development projects.
Developer training
The ContactMonkey Development team undergoes regular secure development training to implement best practices and deliver secure services.
Secure testing
ContactMonkey conducts thorough testing, including penetration testing by internal and external experts, ensuring comprehensive internal communication security assessments.
Cloud security
ContactMonkey employs patented insolation for customer cloud environments, encrypting all data and continuously monitoring the platform for security threats.
Integration with corporate email systems
ContactMonkey’s secure internal communications software seamlessly integrates with corporate email systems such as Microsoft Outlook and Gmail. This enables businesses to leverage existing email infrastructure while adding additional internal email security and functionality.
Audience segmentation
With email segmentation, ContactMonkey allows businesses to organize and divide their internal communication audience based on various criteria such as department, role, or location. This enables organizations to send targeted and relevant messages securely to specific groups within the organization, ensuring that sensitive information is only shared with the appropriate recipients.
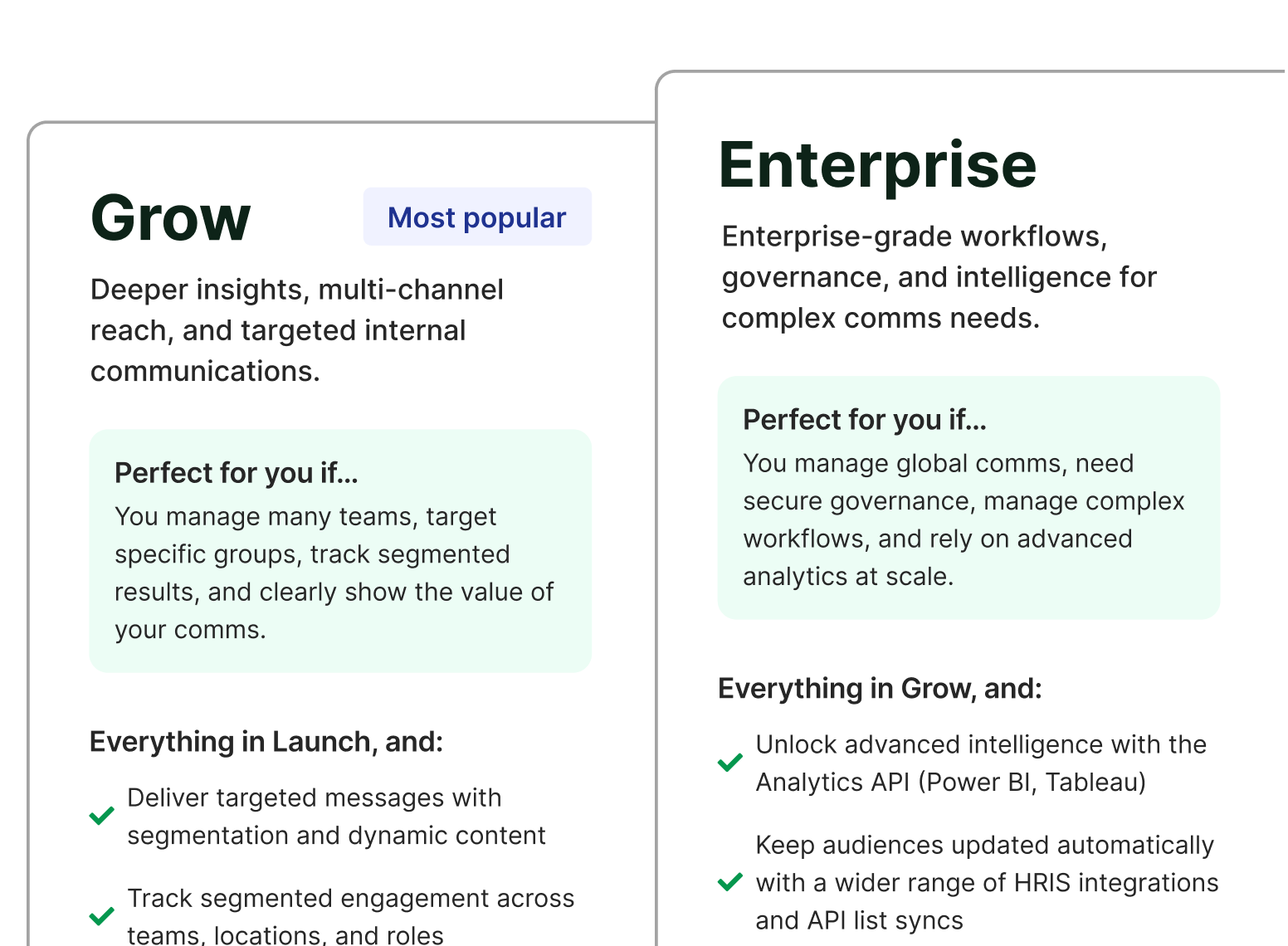
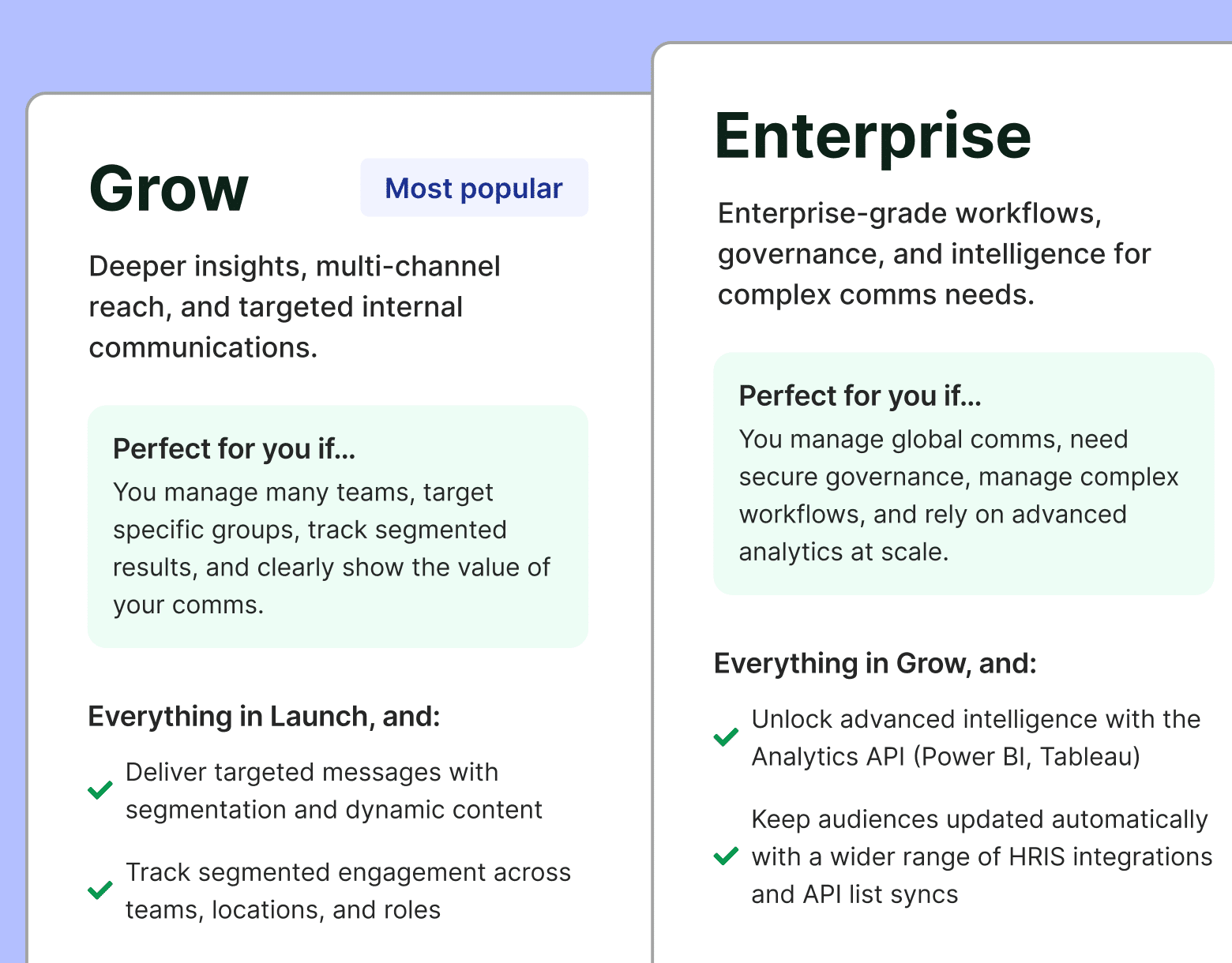
TL;DR: How to Secure Internal Communications
- Protecting your internal communications is crucial: in today’s digital landscape, cyber threats loom large.
- Internal communications security breaches can lead to long-term disruption: data misuse, reputational damage, financial losses, and regulatory penalties are all common outcomes of an internal communications security breach.
- Shielding your communications means implementing robust security measures: encryption, access controls, and secure messaging platforms not only protect sensitive data but also nurture trust among employees, clients, and stakeholders.
- To ensure internal email security, businesses should adhere to best practices: use secure communication software, employ encryption, implement multi-factor authentication, establish access controls, and regularly update software. Employee training and monitoring tools further strengthen defenses against potential breaches.
- ContactMonkey offers a comprehensive solution for secure internal communication: email tracking, SOC 2 compliance, single sign-on authorization, data encryption on AWS, GDPR compliance, and seamless integration with corporate email systems. Get top-tier internal communication security while streamlining your internal communications with ContactMonkey.
Internal communication software and security are closely linked. When your software is not secure, your internal communications – and your entire business – are vulnerable to cyber threats.
ContactMonkey’s all-in-one solution lets you fortify your internal communication channels against potential threats—and protect the privacy and integrity of sensitive information. See how ContactMonkey can secure and streamline your business communications.
Try ContactMonkey for free, today! Book a personalized demo and learn how you can upgrade your IC game and strengthen communications and internal email security with ContactMonkey.